Posted :

- so certbot!? Eh!
what is that really
? is it some kind of certification bot?
- well, hmm, how to put it ? hmm, do you have? do you have some sort of local development server ?
- as in installing nginx, WordPress, MySQL, flask ... as shown in this
article?
- exactly! And it is as simple, as wanting to have ssl locally, maybe as a requirement, or to test something ...
- hey! but can't we use certbot, on a production server as well?
- excellent.
- so how shall we proceed?
- well, certbot can be installed, by using an installer, provided by the
community.
- oh, but what about our development environment?
- shouldn't we like keep everything in one place?
- so what do you propose?
- Cygwin?
- cygwin.
- so maybe just install python3.8, and issue pip3.8 install certbot.
- okay cool, but wait, wait!
What are these errors
that I am seeing!?
Downloading cryptography-3.4.7.tar.gz (546 kB)
Installing build dependencies ... error
ERROR: Command errored out with exit status 1:
command: /usr/bin/python3.8.exe /tmp/pip-standalone-pip-eyjszu7h/__env_pip__.zip/pip install --ignore-installed --no-user --prefix /tmp/pip-build-env-mv504fp9/overlay --no-warn-script-location --no-binary :none: --only-binary :none: -i https://pypi.org/simple -- 'setuptools>=40.6.0' wheel 'cffi>=1.12; platform_python_implementation != '"'"'PyPy'"'"'' 'setuptools-rust>=0.11.4'
cwd: None
...
...
Running setup.py install for cffi: finished with status 'error'
ERROR: Command errored out with exit status 1:
command: /usr/bin/python3.8.exe -u -c 'import io, os, sys, setuptools, tokenize; sys.argv[0] = '"'"'/tmp/pip-install-4uusycx3/cffi_b5ccd93fee024e8f8a8ce6424a318aa8/setup.py'"'"'; __file__='"'"'/tmp/pip-install-4uusycx3/cffi_b5ccd93fee024e8f8a8ce6424a318aa8/setup.py'"'"';f = getattr(tokenize, '"'"'open'"'"', open)(__file__) if os.path.exists(__file__) else io.StringIO('"'"'from setuptools import setup; setup()'"'"');code = f.read().replace('"'"'\r\n'"'"', '"'"'\n'"'"');f.close();exec(compile(code, __file__, '"'"'exec'"'"'))' install --record /tmp/pip-record-umgcv0ba/install-record.txt --single-version-externally-managed --prefix /tmp/pip-build-env-mv504fp9/overlay --compile --install-headers /tmp/pip-build-env-mv504fp9/overlay/include/python3.8/cffi
cwd: /tmp/pip-install-4uusycx3/cffi_b5ccd93fee024e8f8a8ce6424a318aa8/
Complete output (48 lines):
unable to execute 'gcc': No such file or directory
unable to execute 'gcc': No such file or directory
No working compiler found, or bogus compiler options passed to
the compiler from Python's standard "distutils" module. See
the error messages above. Likely, the problem is not related
to CFFI but generic to the setup.py of any Python package that
tries to compile C code. (Hints: on OS/X 10.8, for errors about
-mno-fused-madd see http://stackoverflow.com/questions/22313407/
Otherwise, see https://wiki.python.org/moin/CompLangPython or
the IRC channel #python on irc.freenode.net.)
Trying to continue anyway. If you are trying to install CFFI from
a build done in a different context, you can ignore this warning.
building '_cffi_backend' extension
creating build/temp.cygwin-3.2.0-x86_64-3.8
creating build/temp.cygwin-3.2.0-x86_64-3.8/c
gcc -Wno-unused-result -Wsign-compare -DNDEBUG -g -fwrapv -O3 -Wall -ggdb -O2 -pipe -Wall -Werror=format-security -Wp,-D_FORTIFY_SOURCE=2 -fstack-protector-strong --param=ssp-buffer-size=4 -DOPENSSL_NO_SSL3=1 -fdebug-prefix-map=/pub/devel/python/python38/python38-3.8.10-1.x86_64/build=/usr/src/debug/python38-3.8.10-1 -fdebug-prefix-map=/pub/devel/python/python38/python38-3.8.10-1.x86_64/src/Python-3.8.10=/usr/src/debug/python38-3.8.10-1 -ggdb -O2 -pipe -Wall -Werror=format-security -Wp,-D_FORTIFY_SOURCE=2 -fstack-protector-strong --param=ssp-buffer-size=4 -DOPENSSL_NO_SSL3=1 -fdebug-prefix-map=/pub/devel/python/python38/python38-3.8.10-1.x86_64/build=/usr/src/debug/python38-3.8.10-1 -fdebug-prefix-map=/pub/devel/python/python38/python38-3.8.10-1.x86_64/src/Python-3.8.10=/usr/src/debug/python38-3.8.10-1 -I/usr/include/ffi -I/usr/include/libffi -I/usr/include/python3.8 -c c/_cffi_backend.c -o build/temp.cygwin-3.2.0-x86_64-3.8/c/_cffi_backend.o
unable to execute 'gcc': No such file or directory
error: command 'gcc' failed with exit status 1
...
- packaging?
- packaging.
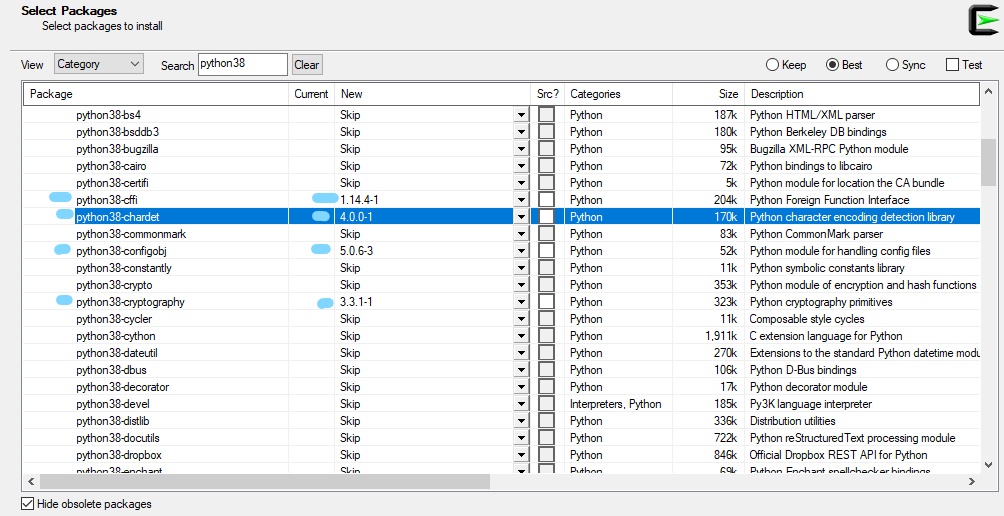
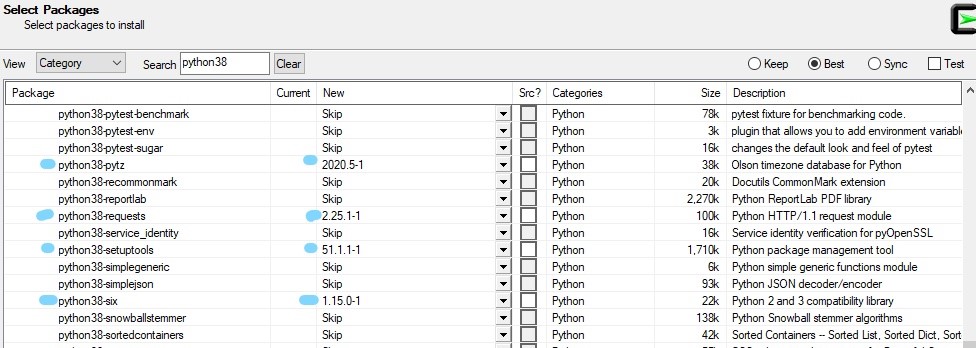
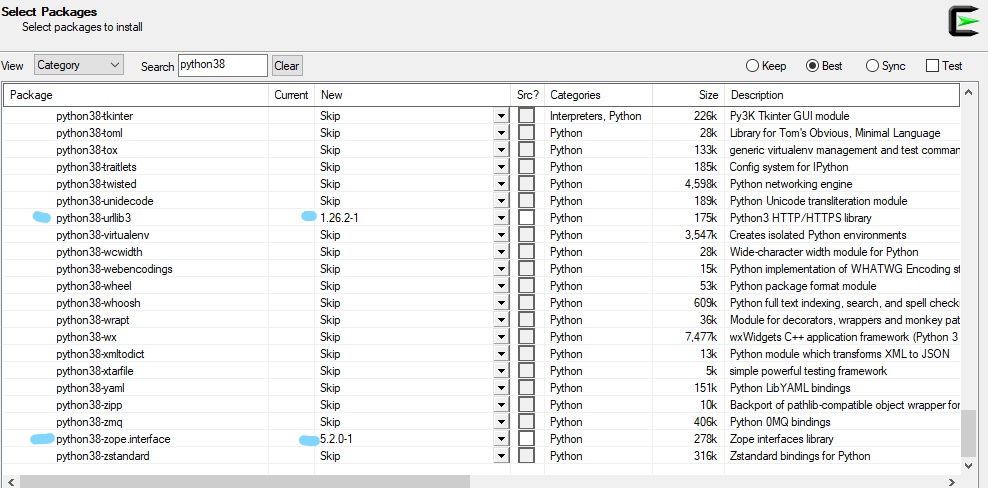
- so what to install using cygwin,
for certbot to work?
python38python38-cffipython38-chardetpython38-configobjpython38-cryptographypython38-opensslpython38-pycparserpython38-pytzpython38-requestspython38-setuptoolspython38-sixpython38-urllib3python38-zope.interface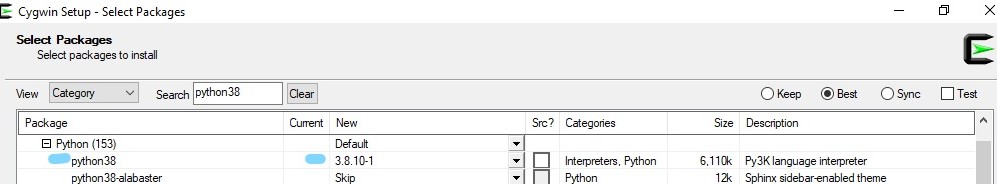

- okay, cool, now what?
- why not give it a try?
- as in?
-
obtain an ssl certificate
for a website?
$ certbot certonly --manual --preferred-challenges dns -d test.difyel.com
# replace test.difyel.com by your website
Saving debug log to /var/log/letsencrypt/letsencrypt.log
Enter email address (used for urgent renewal and security notices)
(Enter 'c' to cancel): your_email@gmail.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please read the Terms of Service at
https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must
agree in order to register with the ACME server. Do you agree?
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: yes
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Would you be willing, once your first certificate is successfully issued, to
share your email address with the Electronic Frontier Foundation, a founding
partner of the Let's Encrypt project and the non-profit organization that
develops Certbot? We'd like to send you email about our work encrypting the web,
EFF news, campaigns, and ways to support digital freedom.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
(Y)es/(N)o: y
Account registered.
Requesting a certificate for test.difyel.com
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Please deploy a DNS TXT record under the name:
_acme-challenge.test.difyel.com.
with the following value:
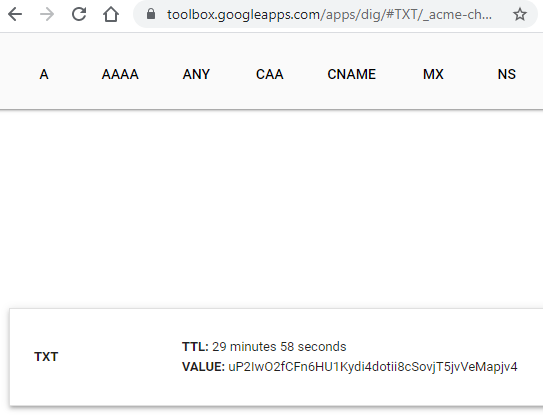
uP2IwO2fCFn6HU1Kydi4dotii8cSovjT5jvVeMapjv4
Before continuing, verify the TXT record has been deployed. Depending on the DNS
provider, this may take some time, from a few seconds to multiple minutes. You can
check if it has finished deploying with aid of online tools, such as the Google
Admin Toolbox: https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.test.difyel.com.
Look for one or more bolded line(s) below the line ';ANSWER'. It should show the
value(s) you ve just added.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Press Enter to Continue
Successfully received certificate.
Certificate is saved at: /etc/letsencrypt/live/test.difyel.com/fullchain.pem
Key is saved at: /etc/letsencrypt/live/test.difyel.com/privkey.pem
This certificate expires on 2021-09-23.
These files will be updated when the certificate renews.
NEXT STEPS:
- The certificate will need to be renewed before it expires. Certbot can automatically renew the certificate in the background, but you may need to take steps to enable that functionality. See https://certbot.org/renewal-setup for instructions.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
If you like Certbot, please consider supporting our work by:
* Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
* Donating to EFF: https://eff.org/donate-le
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
- so in other words,
once the command?
- certbot certonly --manual --preferred-challenges dns -d test.difyel.com
- yes. Is issued. And you arrive to?
- Press Enter to Continue
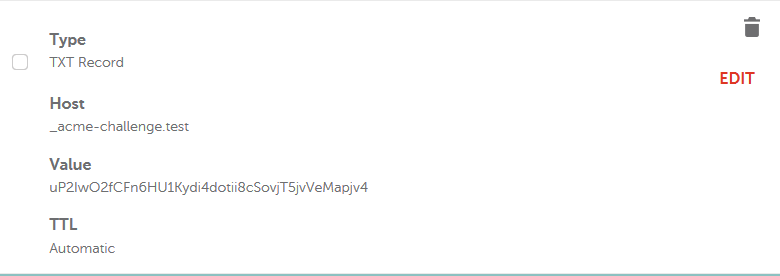
- you must visit your registrar, and add a
text record.
- okay, cool, but make sure
that you select text, for the type of dns record,
and that under the host part, you have ?
- _acme-challenge.test.
- correct, and if this is not a subdomain,
so if this is instead of test.difyel.com
just?
- difyel.com
- correct. You only use?
- _acme-challenge.
- correct. And for the value?
- the value provided by certbot.
- as in?
- uP2IwO2fCFn6HU1Kydi4dotii8cSovjT5jvVeMapjv4
- ohh, okay! interesting ... but how would i know, when to press enter?
- well using another terminal, issue the command?
- nslookup -type=TXT test.difyel.com 8.8.8.8.
- oh look what have i found?
- https://toolbox.googleapps.com/apps/dig/#TXT/_acme-challenge.test.difyel.com
- ah, so this was provided by certbot?
- ahhhh!!!
- so test.difyel.com?
- replace by your website.
- okay, cool, so ..?
- how to configure nginx, to
use these certificates?
- well just make sure, that under your
nginx.conf file, you
have something similar to this:
http {
...
ssl_protocols TLSv1 TLSv1.1 TLSv1.2; # Dropping SSLv3, ref: POODLE
ssl_prefer_server_ciphers on;
ssl_session_cache shared:nginx_SSL:1m;
ssl_session_timeout 1440m;
ssl_ciphers "ECDHE-ECDSA-CHACHA20-POLY1305:ECDHE-RSA-CHACHA20-POLY1305:ECDHE-ECDSA-AES128-GCM-SHA256:ECDHE-RSA-AES128-GCM-SHA256:ECDHE-ECDSA-AES256-GCM-SHA384:ECDHE-RSA-AES256-GCM-SHA384:DHE-RSA-AES128-GCM-SHA256:DHE-RSA-AES256-GCM-SHA384:ECDHE-ECDSA-AES128-SHA256:ECDHE-RSA-AES128-SHA256:ECDHE-ECDSA-AES128-SHA:ECDHE-RSA-AES256-SHA384:ECDHE-RSA-AES128-SHA:ECDHE-ECDSA-AES256-SHA384:ECDHE-ECDSA-AES256-SHA:ECDHE-RSA-AES256-SHA:DHE-RSA-AES128-SHA256:DHE-RSA-AES128-SHA:DHE-RSA-AES256-SHA256:DHE-RSA-AES256-SHA:ECDHE-ECDSA-DES-CBC3-SHA:ECDHE-RSA-DES-CBC3-SHA:EDH-RSA-DES-CBC3-SHA:AES128-GCM-SHA256:AES256-GCM-SHA384:AES128-SHA256:AES256-SHA256:AES128-SHA:AES256-SHA:DES-CBC3-SHA:!DSS";
...
server {
listen [::]:443 ssl http2 ; # Certbot
listen 443 ssl http2 ; # Certbot
...
ssl_certificate /etc/letsencrypt/live/test.difyel.com/fullchain.pem; # Certbot
ssl_certificate_key /etc/letsencrypt/live/test.difyel.com/privkey.pem; # Certbot
... }}
- any
more complete example
?
- sure, you can check this
article.